Designing and deploying architectures for cloud, data centers, and edge locations using both hardware
and software infrastructure has been a cornerstone of my technology experience, spanning both pre- and
post-sales roles throughout my career. One of the key lessons I learned early on is the critical importance
of thoroughly documenting every step of the process as projects progress.
Too often, I've encountered scenarios where technical debt was so significant that I had to spend more
time on discovery than on implementing new solutions, just to avoid downtime and production loss. To
avoid this, I developed a practice of documenting each step throughout the project timeline, rather
than waiting until the end. While this can be a tedious task, it has saved me considerable time and has
been invaluable in troubleshooting issues later. I continue to apply this methodology today, taking
detailed notes during customer meetings, team discussions, and solution-selling engagements to ensure
clarity and efficiency in every phase of the process.
Below are some examples of solutions and architectures I have experience designing and deploying. For
security and data protection reasons, these examples are not tied to any specific customer, but they
provide an overview of the types of projects I enjoy doing!
Modernizing Applications
In my experience with application modernization, I've mainly deployed Rehost, Rebuild, and Revise approaches, with Retire being the next most common strategy. I’ve rarely encountered scenarios where Refactor was the best solution for legacy apps, as it typically requires dedicated developer time—either in-house or outsourced—which can make it more costly. In many cases, it's proven more cost-effective to adopt a SaaS solution or replace the application entirely. Below are a few examples where I’ve successfully Rehosted, Rebuilt, and Revised applications, transitioning them to more modern platforms:
Cloud
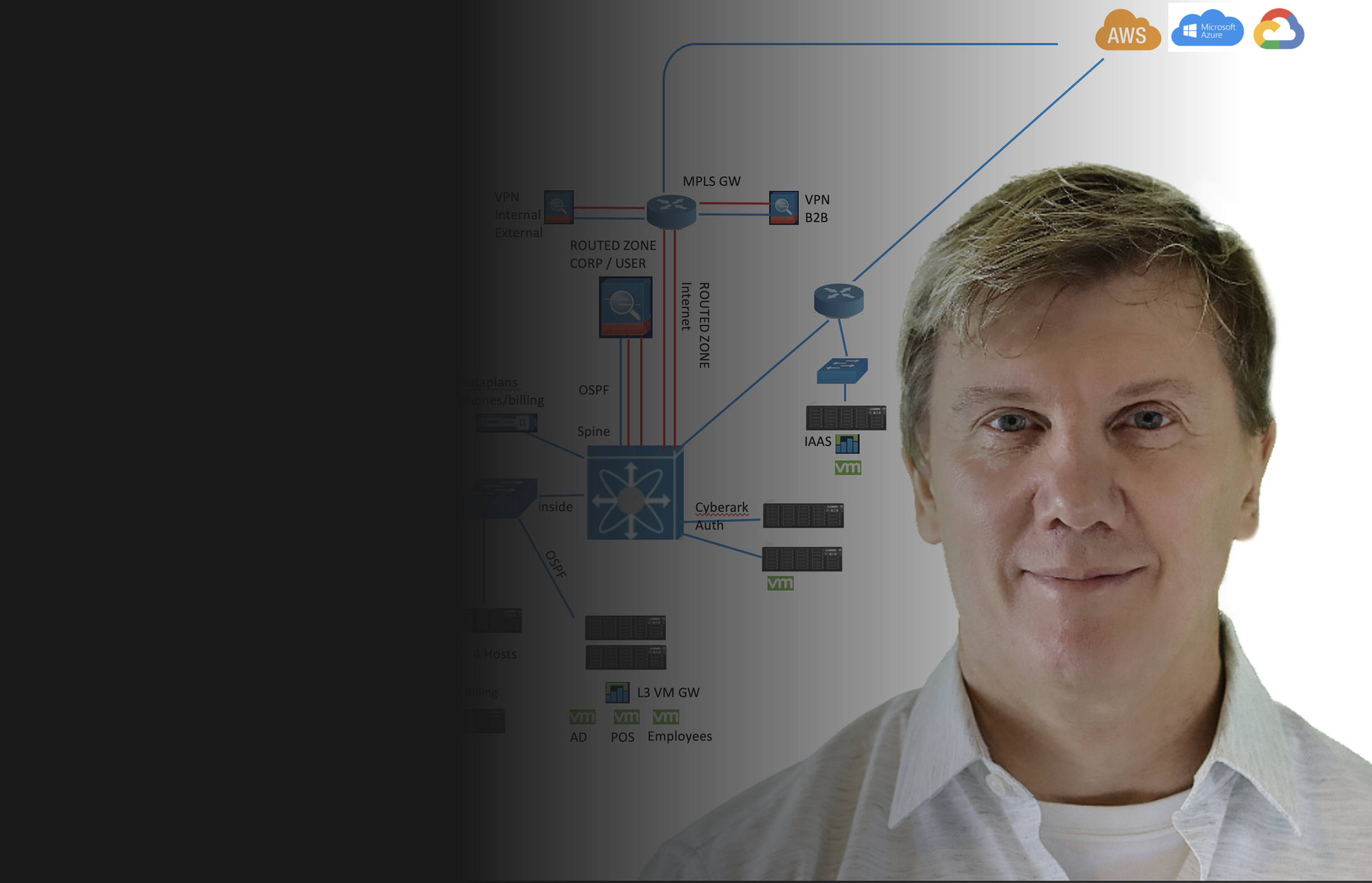
Throughout my career, I have worked extensively with native cloud platforms such
as AWS, Microsoft Azure, and Google Cloud Platform (GCP). I have more experience with AWS, having
worked with it for several years due to customer demand, though Azure and GCP have since caught up.
While AWS remains the primary platform I work with, I also frequently use Azure Resource Manager
(ARM) for customer use cases and deployments.. My experience with GCP has primarily focused
on Google Kubernetes Engine (GKE) and Google Colab for AI training.
Below are a few examples of use cases where I have helped customers leverage public cloud solutions.
The most common scenarios I have worked on include application migrations, disaster recovery,
containerization, data center consolidation, and serverless architecture.
Cloud Architecture Projects
- Data Center Consolidation to AWS
- VM migration from on-prem to AWS/Azure
- East / West Orgs on GCP for DR
- 3 tier app deployment on GKE
- Serverless Lambda functions on AWS
- Model training, RAG using Colab on GCP
Security
Security is a topic that frequently arises in nearly every discussion or
consultation I have with clients. It's one of the most critical considerations in any
design involving people, processes, software, or hardware. In fact, security can be a
deal breaker for any project, regardless of size, if the appropriate measures or
requirements are not properly addressed. Unfortunately, I often see more reactive
approaches rather than proactive when it comes to defining a security framework
for governance or policy enforcement.
From my hands-on experience, I’ve worked with
various aspects of security, including EDR / NDR, intrinsic, zero-trust, certificates,
2 Factor, and identity access management.
Below is an example from one of my security workshops. The slides were used to map out
areas of discussion with multiple teams, prioritize tasks and workflows, then define
a phased approach to implement changes across multiple teams. Once the project was completed,
the customer was very satisfied with the outcome. Some content is missing from the slides
for protection and privacy.
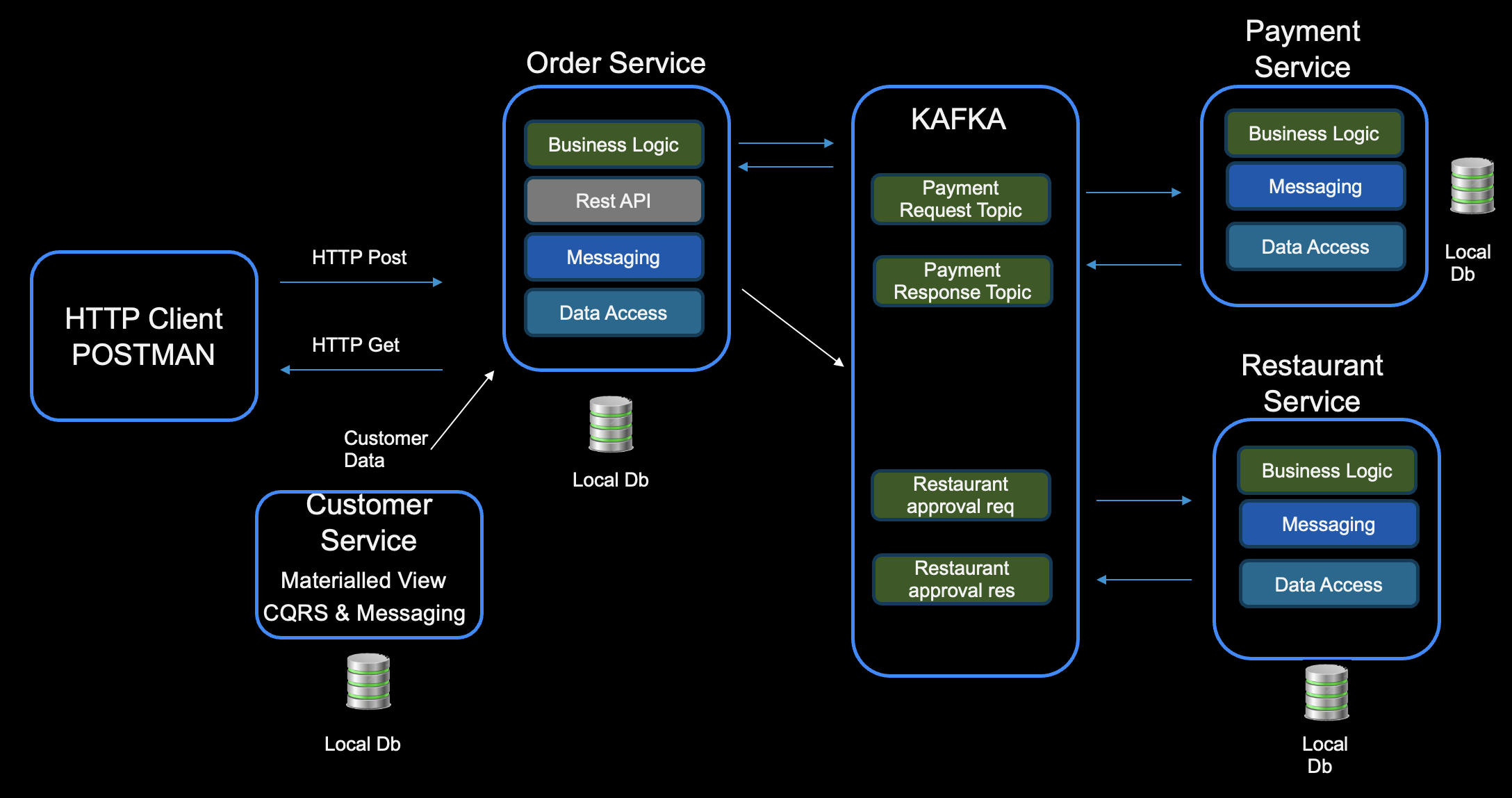
SAGA Pattern
Working with microservices and transactional applications that use REST APIs,
Kafka, and a database backend for payment and ordering services has provided me with valuable
experience in implementing the Saga Pattern and leveraging Hexagonal (Clean) Architecture. Incorporating Clean Architecture
into a system using the SAGA pattern helps in organizing the application in a modular and maintainable
way while still adhering to the principles of distributed transaction management. This ensures that the
business logic, service orchestration, and transaction management are well-structured and loosely coupled.
By combining the SAGA pattern with Clean Architecture, you can build a system where:
- Each service or transaction step is independent and encapsulated
- The orchestration of these steps can be clearly defined and separated from the application logic
- You maintain the flexibility to manage failures and perform compensating actions in a consistent and modular way
The diagram below illustrates an ordering service, which is a project I worked on for a customer.